It may be the health records or your credit card details; everything is stored in the form of a database today. A database is similar to a goldmine for hackers. The main purpose behind any cyber-attack is simply to get access to a database server.
This indicates that the security of the database servers needs to be strengthened and that completely depends on network security, operating system hardening, and physical security. It continues to be a big list but it’s important to learn how to secure your database server first –
- Strong Password Policy Execution –
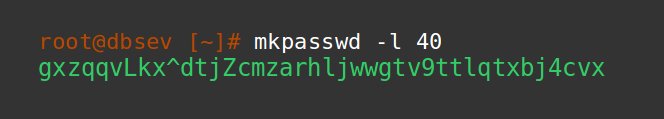
While creating a user enforce your database configuration to REQUIRE a strong password. Some servers have built-in validation features, for example, MSSQL has a built-in password validation feature while some like MySQL forces you to install additional plugins (validate_password plugin).
Execute a password policy that asks a password length of 20+ characters and blocks dictionary words.
- Discard all Default Users and Demo-test Databases –
No doubt all database servers come with a few demo databases as well as users. These databases are public information and therefore, anyone can access your server using these details to collect the database as well as user information.
Immediately delete these databases after you create your own.
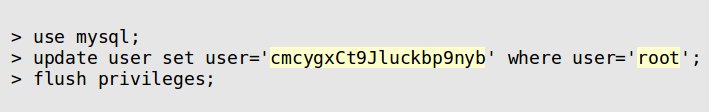
- Change the Admin User Name –
Suppose the attacker knows the admin user name, he can easily guess the password and gain access. Many database servers set the admin username by default and then have to face the consequences. For example – In the case of MySQL, it’s “root”.
For additional security, it’s better to change the admin username.
- User Privileges Need to be Restricted –
Usually, database users created access to all tables available in the database which is required only in a few cases.
Access needs to give to only minimum required tables and privileges (SELECT, INSERT, etc.) should be limited to only what’s actually required by the user. This will help in preventing data loss even after an exploit attempt.
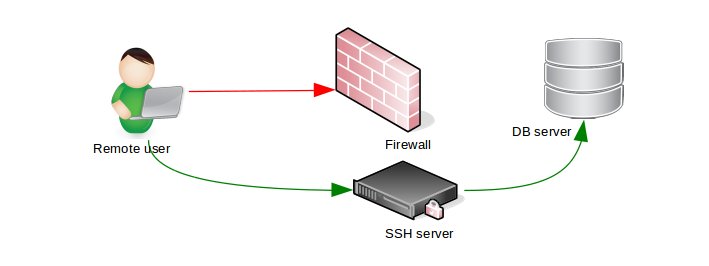
- Disable Public Network Access to Database Servers –
Business applications stored in databases. In the real world, the end users don’t need to access the database directly.
It’s therefore essential to block all public network access to database servers unless you are a hosting provider. Set up gateway servers (SSH tunnels or VPN) for your remote administrators.
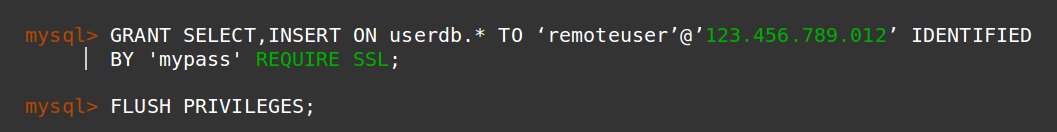
- Enforce SSL/TLS on Remote Connections and Restrict IP –
You will need to open up remote connections if you are a database hosting provider. In such situations, restricting connection by IP and enabling SSL/TLS encryption on database ports is a must.
- Check for Database Dumps in Public Locations –
Leaving the database backups in publicly accessible locations like web folders, temporary partitions, etc. a common mistake done by application owners.
You can detect SQL dump files in public fodders by setting up your monitoring system.
- Encrypt Your Application Files and Backups –
The configuration files of your applications include database access information. If a hacker is able to access the configuration file through application vulnerability, it’s very easy for him to enter the database.
So, it’s better to encrypt all application files and their backups for security.
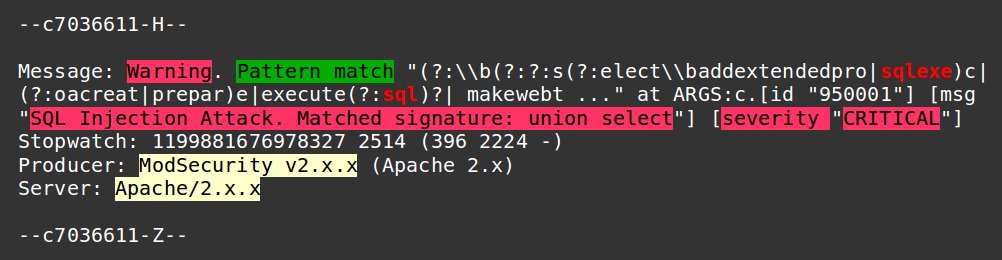
- Web Application Firewall and Malware Scanner Should be used –
In public-facing web applications, database servers are often “back end”. Therefore, attackers use the most common way of web application exploits to access the databases.
Set up Web Application Firewalls like NAXSI, ModSecurity, etc. for blocking all common web application exploits. Additionally, these firewalls integrated with malware scanners (ClamAV) to secure from sophisticated attacks propelled from within the server.
- Always keep the Software Updated –
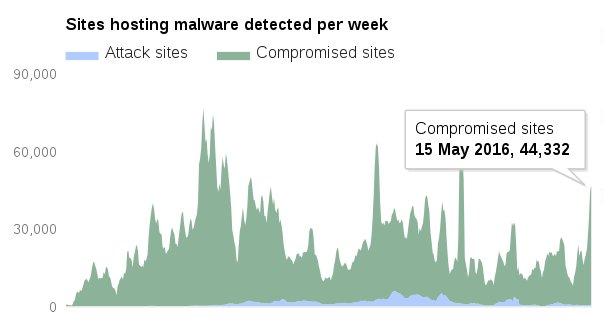
You might think this is something silly. But per Google, it detects 11,000 infected websites per day and the majority of these infections caused due to application vulnerabilities.
So, it won’t be worthless to mention what you already know – install the update urgently after receiving a notification.
Conclusion –
Cybercriminals have become quite intelligent while crafting their attacks. The reason behind their interest in database access is the credit card details and user identities stored which are gold and silver for them. So, ensure you follow the above steps to protect your database server.
